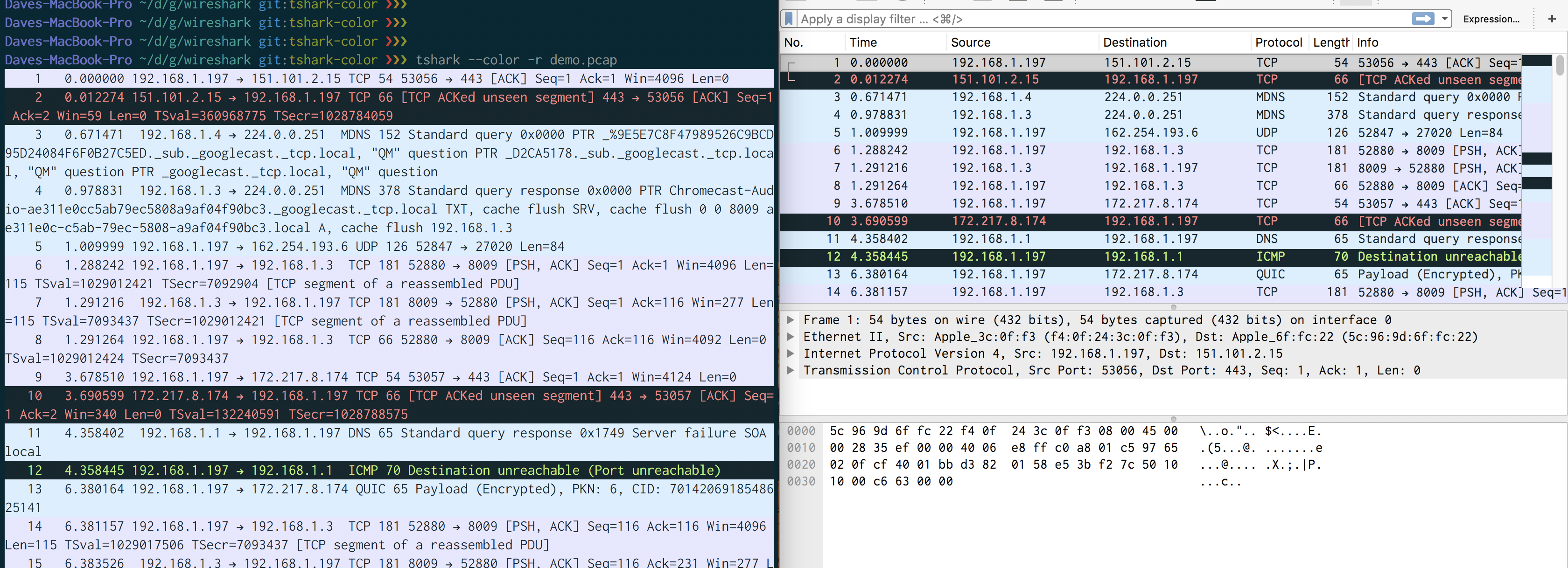
[tl;dr: per-packet coloring is now supported in tshark (command-line
Wireshark) with --color]
I regularly use
tshark
when doing protocol work, often several times per week. It’s a great way to
take load off my brain instead of constantly parsing packets with my eyeballs
directly from a raw hex dump. tshark is like tcpdump on steroids,
providing me the majority of the benefits of Wireshark but without having to
leave the terminal, use the mouse, or slurp a .pcap file around between
machines. With tshark I can usually just view the .pcap file on the same
server I used to capture it.
One feature that is present in Wireshark but has traditionally been missing
from tshark is coloring of packets to help spot noteworthy packets in a
capture. This annoyed me, so I implemented the feature and contributed it to
upstream Wireshark. Here’s what the
result looks like:
Under the hood it works by using a slightly exotic terminal escape sequence to request 24-bit coloring. Also, if you’re a tmux user, you’ll need to upgrade to v2.4 or later if you want to avoid a ragged right edge of background coloring, since tmux only implemented better support for the CSI EL sequence fairly recently
If you want to take this functionality for a spin yourself, you’ll need a
build of tshark from Git that contains commit
v2.5.0rc0-97-g2be411a215.
Then just use tshark as you normally would, but add the --color flag.
Enjoy!
P.S.
Another tshark ProTip™: use -V or -O ${protocol} to get detailed
dissection info in your terminal
Frame 2: 66 bytes on wire (528 bits), 66 bytes captured (528 bits)
Encapsulation type: Ethernet (1)
Arrival Time: Apr 25, 2017 01:45:23.435014000 CDT
[Time shift for this packet: 0.000000000 seconds]
Epoch Time: 1493102723.435014000 seconds
[Time delta from previous captured frame: 0.029217000 seconds]
[Time delta from previous displayed frame: 0.029217000 seconds]
[Time since reference or first frame: 0.029217000 seconds]
Frame Number: 2
Frame Length: 66 bytes (528 bits)
Capture Length: 66 bytes (528 bits)
[Frame is marked: False]
[Frame is ignored: False]
[Protocols in frame: eth:ethertype:ip:tcp]
Ethernet II, Src: 08:35:71:05:d5:30, Dst: f4:0f:24:3c:0f:f3
Destination: f4:0f:24:3c:0f:f3
Address: f4:0f:24:3c:0f:f3
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Source: 08:35:71:05:d5:30
Address: 08:35:71:05:d5:30
.... ..0. .... .... .... .... = LG bit: Globally unique address (factory default)
.... ...0 .... .... .... .... = IG bit: Individual address (unicast)
Type: IPv4 (0x0800)
Internet Protocol Version 4, Src: 54.231.114.156, Dst: 192.168.6.253
0100 .... = Version: 4
.... 0101 = Header Length: 20 bytes (5)
Differentiated Services Field: 0x00 (DSCP: CS0, ECN: Not-ECT)
0000 00.. = Differentiated Services Codepoint: Default (0)
.... ..00 = Explicit Congestion Notification: Not ECN-Capable Transport (0)
Total Length: 52
Identification: 0xb77a (46970)
Flags: 0x02 (Don't Fragment)
0... .... = Reserved bit: Not set
.1.. .... = Don't fragment: Set
..0. .... = More fragments: Not set
Fragment offset: 0
Time to live: 228
Protocol: TCP (6)
Header checksum: 0x6e20 [validation disabled]
[Header checksum status: Unverified]
Source: 54.231.114.156
Destination: 192.168.6.253
Transmission Control Protocol, Src Port: 443, Dst Port: 61617, Seq: 1, Ack: 1, Len: 0
Source Port: 443
Destination Port: 61617
[Stream index: 0]
[TCP Segment Len: 0]
Sequence number: 1 (relative sequence number)
Acknowledgment number: 1 (relative ack number)
Header Length: 32 bytes
Flags: 0x010 (ACK)
000. .... .... = Reserved: Not set
...0 .... .... = Nonce: Not set
.... 0... .... = Congestion Window Reduced (CWR): Not set
.... .0.. .... = ECN-Echo: Not set
.... ..0. .... = Urgent: Not set
.... ...1 .... = Acknowledgment: Set
.... .... 0... = Push: Not set
.... .... .0.. = Reset: Not set
.... .... ..0. = Syn: Not set
.... .... ...0 = Fin: Not set
[TCP Flags: ·······A····]
Window size value: 328
[Calculated window size: 328]
[Window size scaling factor: -1 (unknown)]
Checksum: 0xe37d [unverified]
[Checksum Status: Unverified]
Urgent pointer: 0
Options: (12 bytes), No-Operation (NOP), No-Operation (NOP), SACK
TCP Option - No-Operation (NOP)
Kind: No-Operation (1)
TCP Option - No-Operation (NOP)
Kind: No-Operation (1)
TCP Option - SACK 513-1025
Kind: SACK (5)
Length: 10
left edge = 513 (relative)
right edge = 1025 (relative)
[TCP SACK Count: 1]
_